What Two Functions Describe Uses of an Access Control List
Choose two ACLs assist the router in determining the best path to a destination. Standard ACLs can restrict access to specific applications and ports.
Dynamic ACLs rely upon extended ACLs Telnet and authentication.
. Access-list ACL is a set of rules defined for controlling network traffic and reducing network attacks. What are two uses of an access control list. ACLs can control which areas a host can access on a network.
What two functions describe uses of an access control list. What two functions describe uses of an access control list. Below are some additional reasons why a company might use access control lists.
ACLs provide a basic level of security for network access. There are two types of ACLs. D ACLs can permit or deny traffic based.
Choose three access list number between 1. What two functions describe uses of an access control list. What two functions describe uses of an access control list.
Choose two ACLs can control which areas a host can access on a network. Choose two ACLs assist the router in determining the best path to a destination. What two functions describe uses of an access control list.
Filesystem ACLs filter access to files andor directories. ACLs provide a basic level of security for network access. Vuzvespa S2 - Chapter Exam Access Control Lists CCNAv5.
1What two functions describe uses of an access control list. Perform the tasks in the activity instructions and then answer the question. A ACLs assist the router in determining the best path to a destination.
Examples include IP IPX ICMP TCP UDP NETBIOS and many others. Access control lists can help organize traffic to improve network efficiency and to give network administrators granular control over users on their computer systems and networks. ACLs assist the router in.
These lists permit access to a user to a source or destination only if. ACLs can control which areas a host can access on a network. Access Functions by category.
ACLs assist the router in determining the best path to a destination. ACLs can permit or deny traffic based upon the. An access control list ACL contains rules that grant or deny access to certain digital environments.
Standard ACLs can restrict access to specific applications and ports. Access control list name depending on the router it could be numeric or combination of letters and numbers A sequence number or term name for each entry. Access control lists in networking offer privacy security and simplicity for large corporations that house large amounts of data.
Manually add the new deny ACE with a sequence number of 15. ACLs can permit or deny traffic based upon the MAC address originating on the router. ACLs can control which areas a host can access on a network.
ACLs provide a basic level of security for network access ACLs can permit or deny traffic based upon the MAC address originating on the router. B Standard ACLs can restrict access to specific applications and ports. Filesystem ACLs tell operating systems which users can access the system and what privileges the users are allowed.
3 Launch PT Hide and Save PT Open the PT Activity. What two functions describe uses of an access control list. Networking ACLs filter access to the network.
ACLs provide a basic level of security for network access. Which three values or sets of values are included when creating an extended access control list entry. A network protocol and associated function or ports.
Standard ACLs can restrict access to specific applications and ports. This type of ACLs are often referred to as Lock and Key and can be used for specific timeframes. Standard ACLs can restrict access to specific applications and ports.
A statement of permission or denial for that entry. ACLs can permit or deny traffic based upon the MAC address originating on the router. Create a second access list denying the host and apply it to the same interface.
ACLs provide a basic level of security for network access. ACLs provide a basic level of security for network access. ACLs are used to filter traffic based on the set of rules defined for the incoming or outgoing of the network.
They are arranged first by group and then are arranged alphabetically at the end of this article. This article contains links to articles that provide details about common functions used in expressions in Microsoft Access. ACLs provide a basic level of security for network access.
ACLs can control which areas a host can access on a network. Add a deny any any ACE to access-list 1. C ACLs provide a basic level of security for network access.
ACLs can also be used to improve network security by keeping out malicious traffic. A network administrator needs to configure a standard ACL so that only the workstation of the administrator with the IP address 1921681523 can access the virtual terminal of the main router. S2 Chapter 9.
Choose two ACLs assist the router in determining the best path to a destination. One of the most important functions of access control lists is the ability to prevent unauthorized users from accessing sensitive services or.

Uopmaterials Exam Guide Assignments Final Exams
Configuring Access Control Lists Acls

Stl Sort C Programming Geekboots Algorithm Learn Programming Computer Programming
Access Control Lists Acl In Linux Geeksforgeeks

Essay Example Business Report Format Thatsnotus Throughout Simple Business Report Template 10 Professional Tem Essay Examples Report Template Essay Format

Human Body Systems Review Activity Human Body Systems Body Systems Life Science Lessons

Access Control Models Uhwo Cyber Security

What Is Access Control List Acl Types Linux Vs Windows Imperva
Configuring Access Control Lists Acls

Configuring Access Control Lists Acls

Quality Assurance Plan Template New Quality Assurance Plan Checklist Free And Editable Template Checklist Template Report Template Business Plan Template
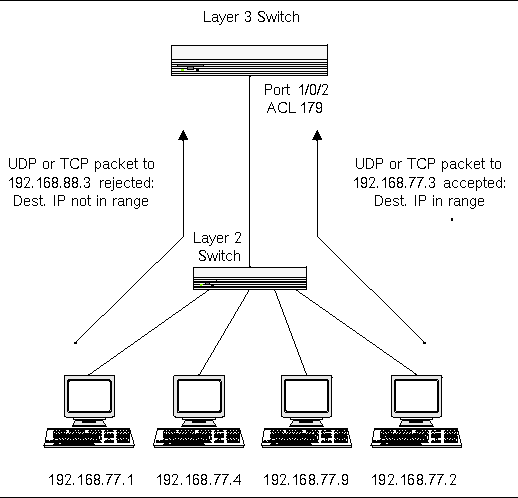
Configuring Access Control Lists Acls

Ms Access Input Mask In Query Form Or Report Computer Help Internet Phone Access Database
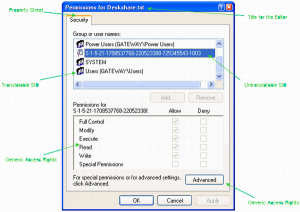
Access Control Models Uhwo Cyber Security

Cool Crafting A Great Assistant Store Manager Resume Job Description Manager Resume Assistant Manager
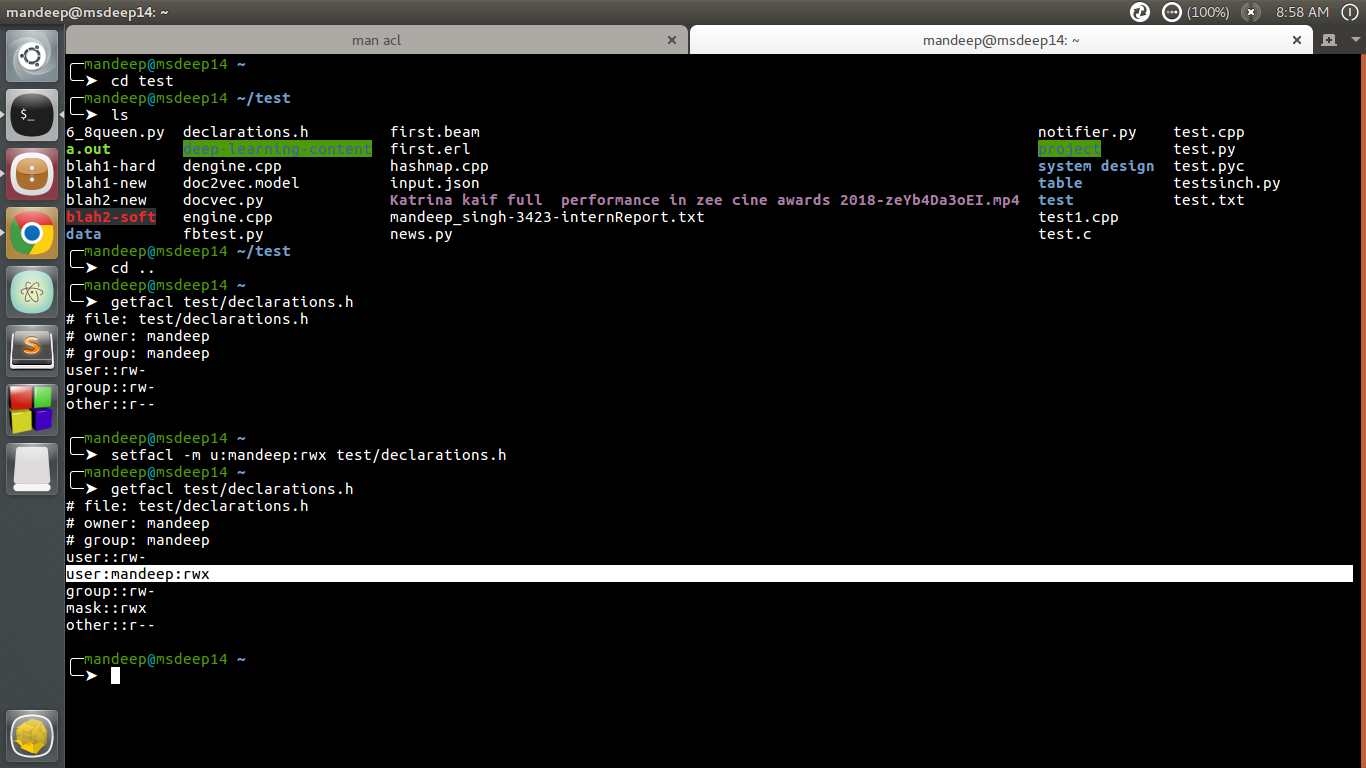
Access Control Lists Acl In Linux Geeksforgeeks

Create A Data Visualizer Diagram In 2022 Flow Chart Process Map Excel



Comments
Post a Comment